
Policy Keys
Settings of the application can be set under "My Account" at this web site. These settings can be overruled by local policy settings, which can be preferred in complex environments or if company policy forbids having data in the cloud (this web site). Offline mode will disable all interaction with this cloud service, including "My Account" configuration. Policies are set under the registry key HKEY_LOCAL_MACHINE\Software\FastTrack Software\Admin By Request\Policies and must be set using the Group Policy editor as shown below. KeyPath must be "Software\FastTrack Software\Admin By Request\Policies".
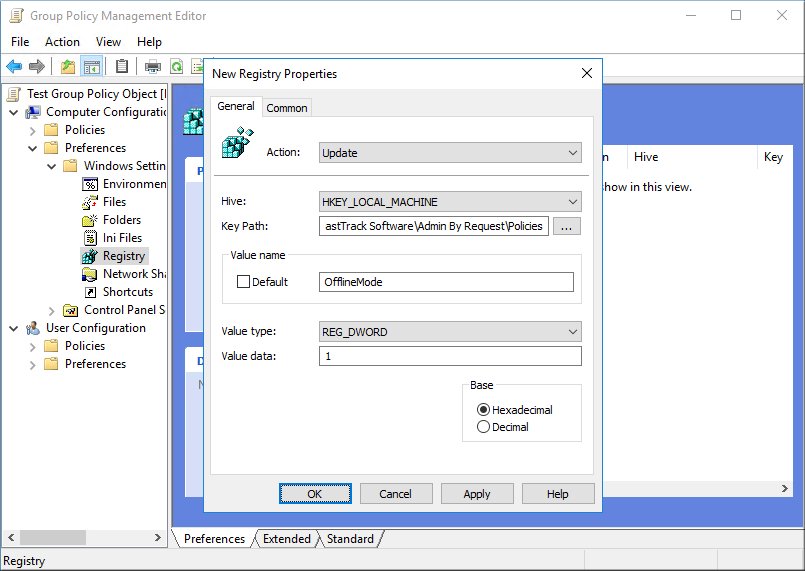
Policy registry values
The basic settings found under "My Account" here on this web site, can be overruled using similar policy registry keys. Offline Mode will completely disable all interaction with the cloud service on this web site.
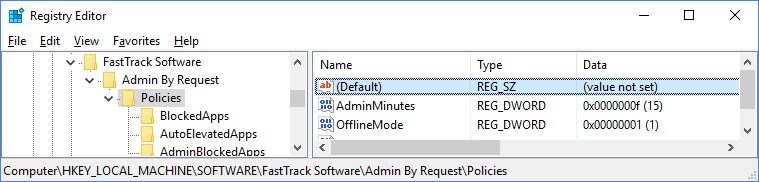
| KEY | TYPE | DEFAULT | VALUE |
| OfflineMode | REG_DWORD | 0 | Disables interaction with this web site entirely, if this value is 1. No inventory data are sent to the cloud and auto-approve is automatically enabled. |
| AutoApprove | REG_DWORD | 0 | Enables automatic approval, if this setting is 1. In offline mode, this setting is automatically enabled. If not configured or value is 0, cloud settings are used. |
| AdminMinutes | REG_DWORD | 15 | Number of minutes the user is administrator. |
| Language | REG_SZ | Auto | User interface language. Default is to use the same language as Windows. Forced language codes are English (EN), German (DE) or Danish (DA). |
| EnableUAC | REG_DWORD | 1 | Enables UAC, if it is not enabled. |
| DesktopIcon | REG_DWORD | 1 | Disables and removes the desktop icon created by Admin By Request. |
| IconName | REG_SZ | Overrules the default name of the desktop and programs icon. Note that the default icon name is localized. | |
| LogFile | REG_SZ | Optional log file. Every time a user elevates, it will be logged to this file. Useful in offline mode, where usage is not reported to the web site. | |
| UserGroups | REG_SZ | If defined, the user must be member of at least one of these groups. | |
| UserOUs | REG_SZ | If defined, the user must be located in one of these organizational units, or an OU under it. Multiple OUs must be split by comma. | |
| ComputerGroups | REG_SZ | If defined, the computer must be member of at least one of these groups. | |
| ComputerOUs | REG_SZ | If defined, the computer must be located in one of these organizational units, or an OU under it. Multiple OUs must be split by comma. |
Group and OU delimiter
Multiple groups or OUs must be split by a vertical pipe, such as "Domain Admins|Customer Relations". This is because comma may naturally appear in groups or OU names and always appears in full distinguished names for OUs. OUs can be specified as full distinguished name or simply the OU name itself. Note that if a OU name is not unique, the check will happen on either. In a list, the user/computer must be member of one (not all) to allow administrator elevation. Note that local users (except Administrator) can not elevate, when domain groups or OUs are in place. Users can always request a PIN code for elevation, in case of an exception.
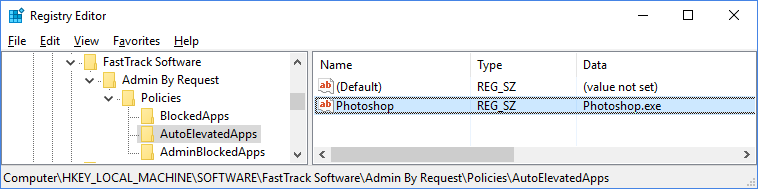
Auto elevated applications
Some legacy applications may always need to run as administrator. A list of applications can be set using policies. For example, if Photoshop always needs to run as administrator (regardless of other settings), a name/data entry can be set under the subkey "AutoElevatedApps". Only the value is used and it can be a full path to an exe file or just the exe file. The user will be prompted for credentials on application start and must enter their user name and password. This credentials prompt is a UAC limitation that cannot be bypassed. But the application will run as elevated administrator without the user being administrator.
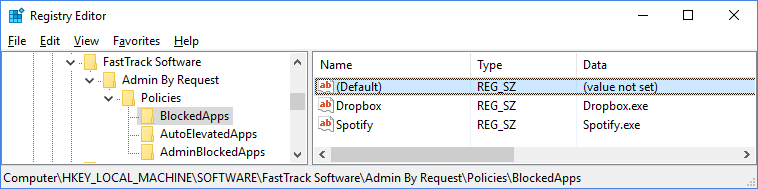
Blocked applications
Applications that are never allowed to run, can be set using the "BlockedApps" subkey. These are applications that will always be blocked from execution, regardless of being elevated or not.
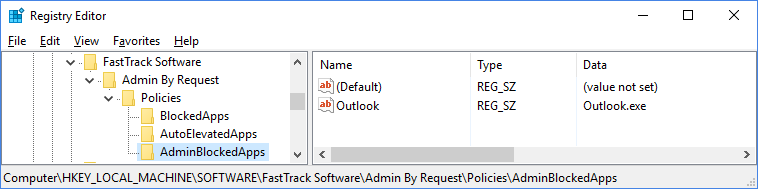
Admin blocked applications
Applications can be blocked, only when the user is elevated by Admin By Request and only when user runs the application as administrator. For example, if the user elevates to administrator, it would make sense to block Outlook.exe, so the user does start Outlook and click dangerous links. Browsers could also be blocked, if the policy is that the must download software before elevation, to try to sandbox the installation as much as possible. Note that a domain administrator can still log on and run this application elevated. It intentionally only applies to users elevating using Admin By Request.
You will get a personal trial Admin By Request web inventory login and Admin By Request client to install on your test computer. This set up will be fully functional for 7 days.
